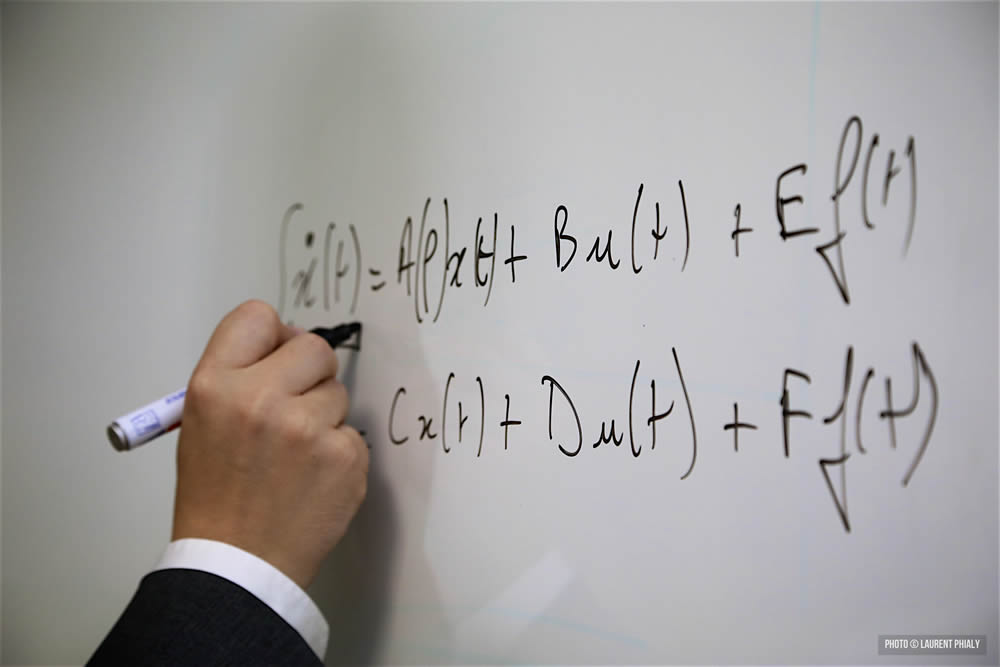
The CID department brings together all the research activities of the CRAN focusing on Automatic Control of Continuous and Cyber-Physical Systems. A wide range of topics is covered, including: modeling, identification, analysis, control, observation, diagnosis, and fault tolerance.
The research work of the CID department is predominantly theoretical and methodological in nature, using a wide range of mathematical tools and dedicated physical models for systems theory to address major challenges arising from increasing complexity and integration of systems. This abstraction and use of common tools constitute a strong and coherent link within the CID department.
These research themes are primarily motivated by strong strategic and societal concerns with significant socio-economic impact. Indeed, some fundamental aspects or formalisms in systems theory are inseparable or even stem from concrete and industrial applications. New, increasingly complex systems are emerging, posing significant scientific challenges for which Automatic Control must provide innovative solutions. A large portion of these applications is associated with the fourth industrial revolution, also known as the future factory, highlighting the importance of integrating digital sciences into everyday life and industry. Beyond embedded systems, interconnected, multi-agent, or cooperative systems are becoming more widespread, as are event-driven systems. Additionally, Automatic Control aims to expand beyond its traditional industrial application sectors (energy management, smart city, steelmaking, etc.) by venturing into diverse application domains such as health (oncology, neurology, surgery, etc.), sociology (social behavior, opinion dynamics, etc.), finance, future transportation (future cars and airplanes), and sustainable development (circular economy, ecological systems). The CID department contributes to these applications by proposing efficient tools while considering increasingly stringent implementation and security constraints.
The research themes are grouped into two projects.
- Model-Based Control and Observation and Optimization (MODEL)
- Data-Driven Modeling, Control, and Decision Making (DATA)


